EU GDPR, Cyber & Information Security rises to the top of leaders 'to do' list
Addressing the strategic requirements for EU GDPR means you need an Information Security Management System (ISMS) that works well. You can do it with pam.
Implement and manage an integrated ISMS from one secure place
Prepare for and practice EU GDPR
Follow ISO 27001, NIST, PCI, HMG SPF and other compliance regimes easily
Ensure taxpayer money is directed to front line services and mitigate the risk of large EU GDPR fines from breaches internally or through suppliers
Collaborate internally and externally to demonstrate integrity in the supply chain
Be a responsible customer and encourage suppliers to implement an ISMS you can both trust
Prepare for EU GDPR and demonstrate accountability
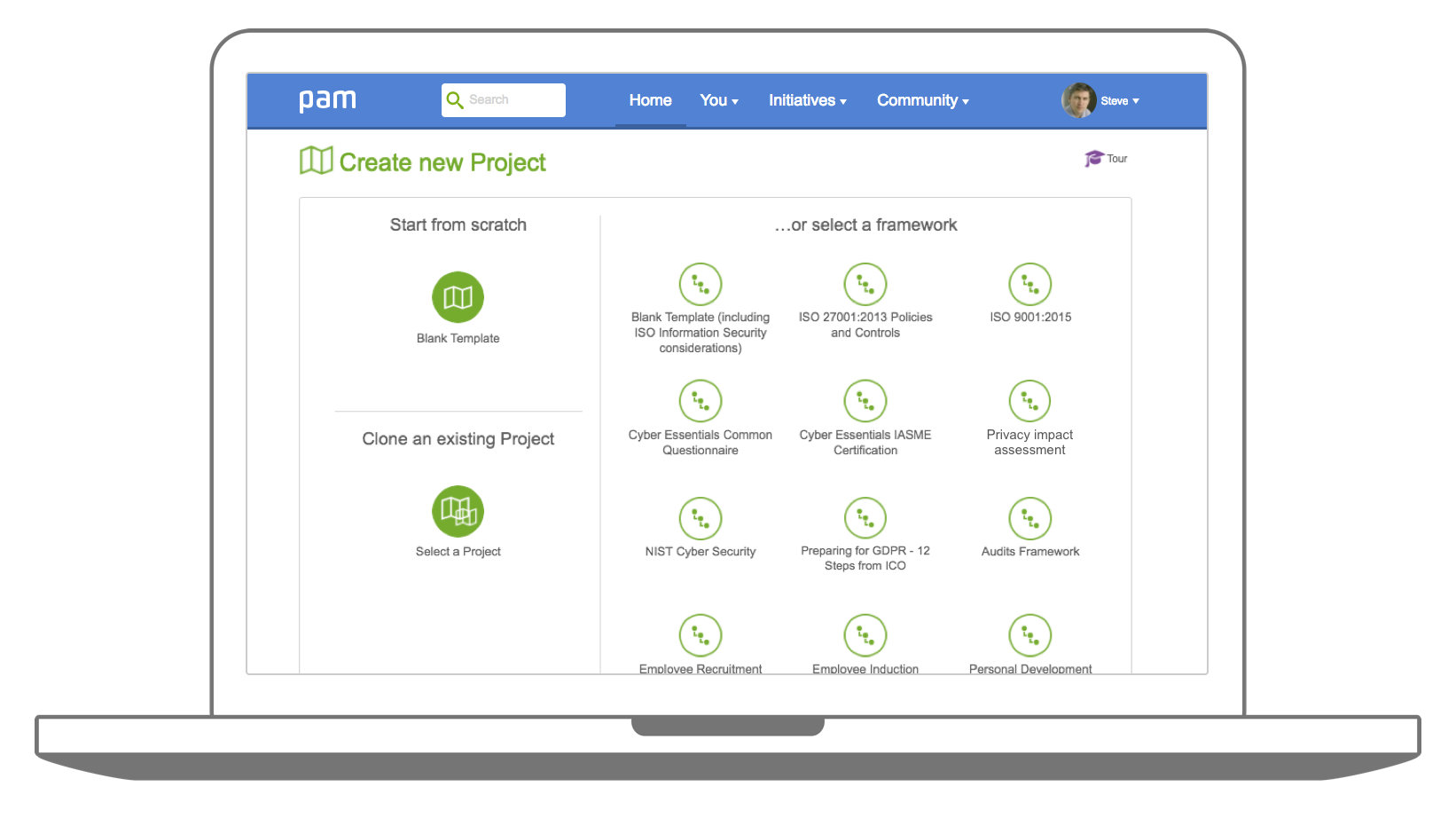
- Save time and hassle by loading a prebuilt 12 steps framework as suggested by the ICO, in just seconds
- Use collaborative areas to work better together with colleagues on addressing the 12 steps with tasks, discussions, document management and notes recording
- Demonstrate your accountability with effective audit trails, governance and compliance embedded in the way you work
- Integrate your 12 Steps with other EU GDPR and information security related work quickly and easily
- Use the project planning and action management capability to assign actions, owners, deadlines and see progress
- Drive out cost, waste and risk to focus on exactly what you need to do for success and plan your priority investments
I don't know if this is going to make my life complete or just a whole lot better...
Home Office Accreditor
Practice key aspects of EU GDPR
- Awareness communications and engagement
- Information audits and improvements
- Policy & procedure development and administration
- Subject access requests (and FOI)
- Data breach and security incident management
- Protection & privacy by design (PBD)
- Privacy Impact Assessment (PIA) and risk management
- Data processor and supply chain management
- Demonstration of 'approved' certifications e.g. ISO 27001
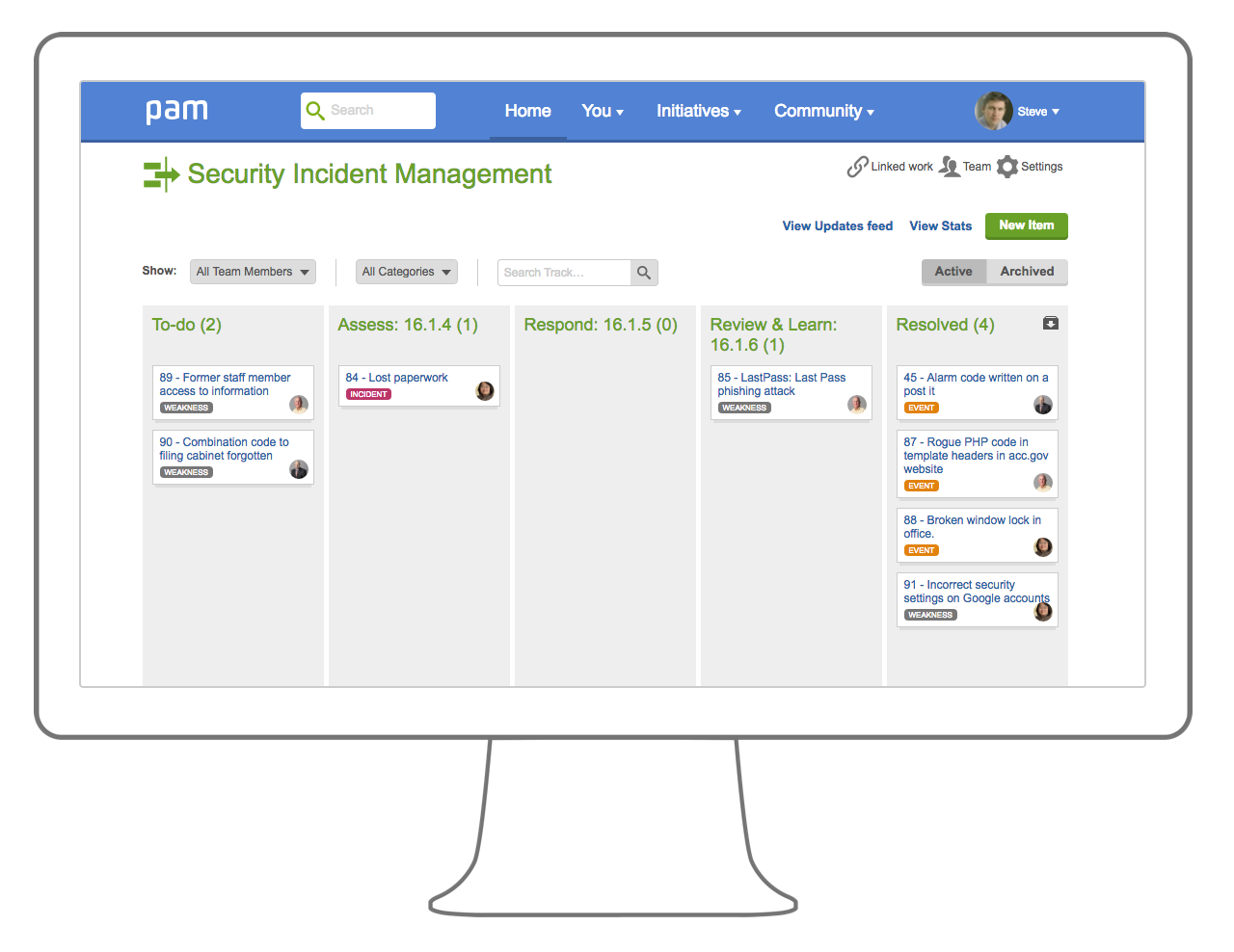
GDPR drives the need for compliance with 'approved' certifications like ISO 27001
ISO 27001:2013 (or an equivalent standard) goes a long way to demonstrating security & assurance for EU GDPR.
You can implement and manage your whole ISMS securely in the cloud, alongside our integrated GDPR compliant additional features (e.g. PIA, PBD etc).
Comply with key Articles from the regulation around security of personal data and demonstrate readiness for independent certification (e.g. UKAS) if desired for ISO 27001.
It's a fraction of the cost of other solutions and will get you better results faster than you could achieve alone.
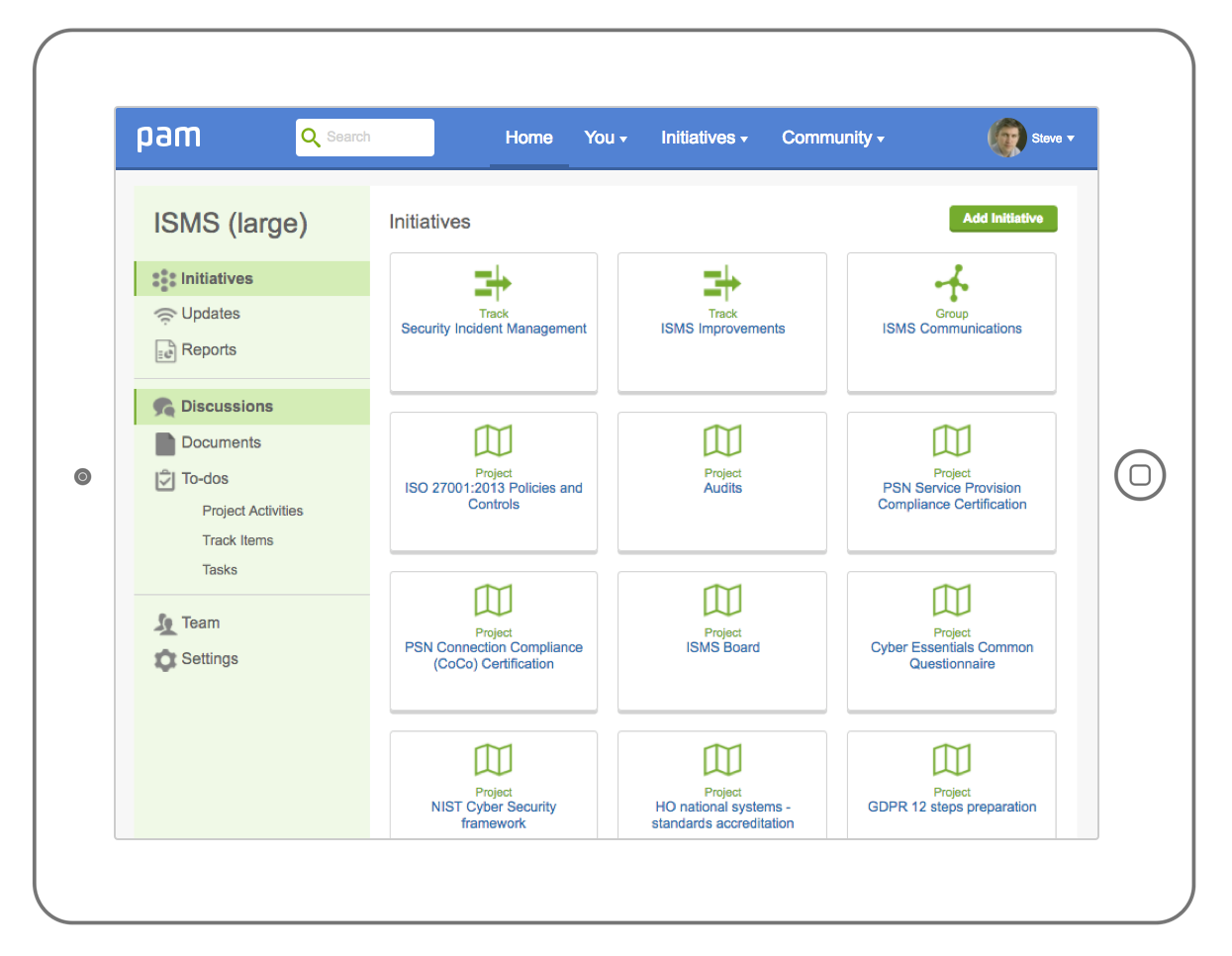
Adopt one or more parts of the platform to complement your existing capabilities:
- Manage all the requirements, controls and policies
- Identify and address risks, interested parties and applicable legislation
- Demonstrate information security and privacy by design in projects
- Undertake corrective actions and improvements
- Manage security incidents including notifications to the ICO
- Update, engage and task staff and others around information security
- Manage HR security over the lifecycle
- Demonstrate management of information security in the supply chain
Demonstrate control of (and support for) your supply chain
EU GDPR puts far greater emphasis on data processors as well as controllers. Whilst you can outsource responsibility for performance, you can't abdicate accountability or avoid reputational and financial consequences for your suppliers getting it wrong.
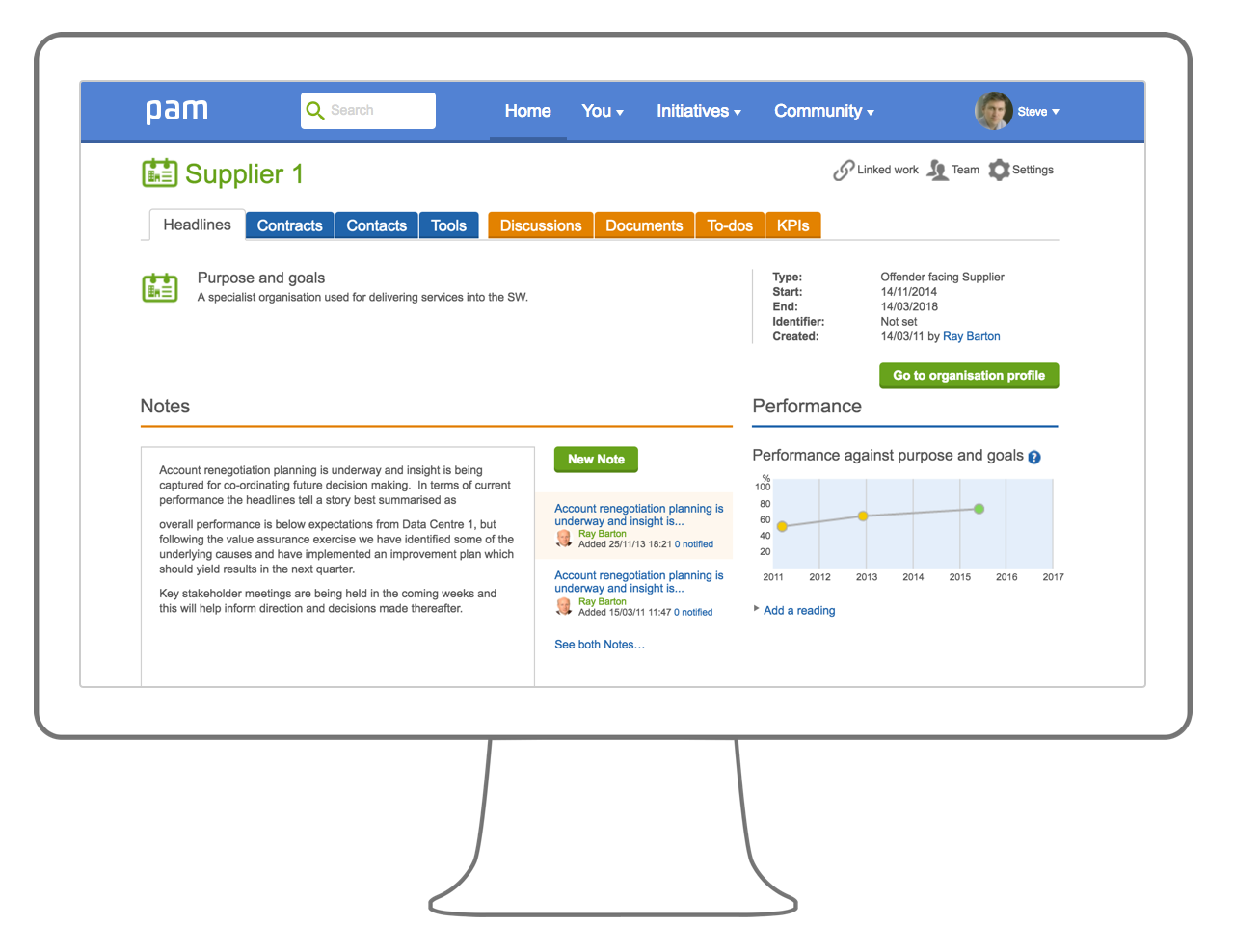
We can help you do the following:
- Control your supply chain well with integrated supply chain management
- Engage and collaborate with the suppliers on work to get done and align on key parts of the ISMS
- Build and manage supply chain clusters to demonstrate end to end assurance
- Allow very small suppliers to leverage your ISMS to save cost together and lower risk
- Alternatively incentivise suppliers to adopt pam or ISMS.online (our sister service) to run their own ISMS and we will discount the service as part of an integrated service with you
this solution puts affordable and trusted information security practices within the reach of all organisations, from the smallest micro business through to large enterprise. That has to be a great thing for public sector confidence and assurance where government agencies want to work more with SME's but are (generally) increasing information security risks by doing so.
Mark Darby CEO Alliantist
